Find out how to protect your WordPress blog from XML-RPC pingback abuse.
This week it was revealed by security firm Sucuri that over 162,000 WordPress websites were being used as part of a DDoS attack.
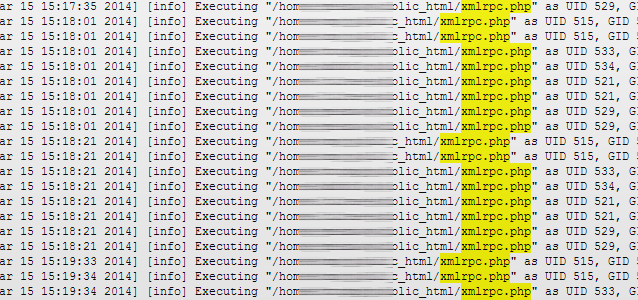
This is not the first time the XML-RPC pingback function has been used as part of a DDoS attack.
Personally however, monitoring server logs today showed a significant increase in XML-RPC abuse on various WordPress blogs on my server, which may be the case also for other people.
In the future WordPress should hopefully update to protect sites from this issue, but in the meantime here is a list of some of the options available.
How to Protect Your WordPress Blog from XML-RPC Pingback Abuse
You can protect your blog in various ways - using either a few lines of code, or via a WordPress plugin.
1) Not recommended: Completely Remove XML RPC
This option will totally remove the XML-RPC functionality.
This may not necessarily be the best option, as it may affect your use of Jetpack and any mobile apps you use.
However if you are sure it will not cause problems for you, it is possible to remove XML-RPC by one of the following methods.
a) Block access via .htaccess file
Technically this does not remove XML-RPC, so much as blocking access to it.
Add the following to your .htaccess file:
<Files "xmlrpc.php">
Order allow,deny
Deny from all
</Files>Code language: HTML, XML (xml)b) Use the Disable XML-RPC WordPress Plugin
A quick and simple way to remove XML-RPC functionality completely using a WordPress plugin.
Jump to: Disable XML-RPC Plugin @ WordPress.org
c) Add Filter To WP-Config
As per this article, you can add the xmlrpc_enabled return false filter to disable XML-RPC fully.
In your wp-config.php file add:
add_filter('xmlrpc_enabled', '__return_false');Code language: JavaScript (javascript)After the line:
require_once(ABSPATH . 'wp-settings.php');Code language: PHP (php)2) Disable XML-RPC Pingback Service
Specifically disabling the XML-RPC pingback service should mean that all other functions will continue to work.
The following options show you some of the ways of doing this.
Note: You may want to check also that your theme or another plugin isn't hard-coding in an XML-RPC pingback link.
a) Use the Disable XML-RPC Pingback WordPress Plugin
A quick and easy way of stopping XML-RPC pingback functionality is to install the Disable XML-RPC Pingback plugin.
Jump to: Disable XML-RPC Pingback Plugin @ WordPress.org
b) Add Filter to Functions.php
You can remove the XML-RPC pingback functionality specifically by adding the following to your functions.php file (or a custom plugin):
function remove_x_pingback($headers) {
unset($headers['X-Pingback']);
return $headers;
}
add_filter('wp_headers', 'remove_x_pingback');Code language: PHP (php)I hope you found this page useful!
More information on the recent DDoS attacks: